Abstract
The global Internet infrastructure is a complex system that requires collaboration and responsible action from various stakeholders to maintain its health and stability. One of the critical challenges faced by the Internet ecosystem is the leakage of DNS reverse lookup traffic related to private IP addresses. This paper proposes the deployment of AS112 nodes as a technical solution to address this issue and invites other networks to adopt a similar approach, contributing to a more resilient and efficient Internet.
Introduction
The Internet is an essential part of our daily lives, and organizations managing large networks play a significant role in ensuring a stable and reliable user experience. DNS reverse lookup traffic associated with private IP addresses, as defined in RFC 1918 and RFC 6598, often leaks onto the public Internet due to misconfigurations and other factors. This unintended traffic unnecessarily loads the global DNS infrastructure and impacts overall network performance. AS112 nodes offer a distributed sinkhole service, absorbing this traffic and mitigating its effects on the Internet ecosystem.
What is AS112?
Imagine you accidentally dial a phone number that doesn’t exist. Instead of reaching someone, you’d expect to hear a message saying the number isn’t in service. Now, think of the internet as a massive phone book, but instead of phone numbers, we have addresses for websites and online services. Sometimes, people or systems mistakenly try to reach addresses that don’t exist or are reserved for private use (like a private phone line that’s not listed in the public directory).
AS112 is like a friendly operator in this vast online phone system. Instead of letting these mistaken calls bother the main switchboard (the root of the internet), AS112 steps in and says, “Hey, that address doesn’t exist or is private. Please check and try again.” By doing this, AS112 helps reduce unnecessary traffic and ensures the main switchboard isn’t overwhelmed with these mistaken calls.
Why is AS112 Important?
-Reducing Unnecessary Traffic: Just like a busy phone line, the internet can get clogged with too many requests. By handling these mistaken calls, AS112 ensures the main system runs smoothly.
-Protecting the Core of the Internet: The root of the internet is vital for everyone’s online activities. AS112 acts as a guardian, ensuring that the root is not burdened with irrelevant requests.
-Helping Systems and People: By responding to these mistaken requests, AS112 provides feedback, which can help in identifying and fixing errors.
In essence, AS112 is like a helpful operator in the vast world of the internet, ensuring everything runs smoothly and efficiently.
Technical Solution
AS112 nodes are strategically placed within a network to handle and absorb misdirected DNS reverse lookup traffic for private IP addresses. By deploying these nodes, organizations can offload unintended traffic and reduce the burden on local and global DNS infrastructure. The implementation of AS112 nodes involves the following steps:
- Determine optimal locations for AS112 nodes based on traffic patterns and network topology.
- Configure the AS112 nodes with appropriate software, such as BIND or Knot DNS, to handle reverse DNS lookup traffic for the specific private IP address ranges.
- Advertise the AS112 prefix in the global routing table through the organization’s Autonomous System (AS) to attract misdirected traffic.
- Monitor the AS112 nodes to ensure they handle the reverse lookup traffic effectively and adjust configurations as needed.
Deployment Recommendations for AS112
IP Address Choice
Use the dedicated IP addresses assigned for AS112 nodes. This ensures that the node is recognized as part of the AS112 project and can handle the specific traffic directed towards it.
Use of BGP (Border Gateway Protocol)
BGP should be used to announce the presence of the AS112 node to neighboring networks. This helps in directing the appropriate traffic to the node.
It’s recommended to use BGP communities to control the scope of the announcement, ensuring that it reaches the intended audience.
Network Environment Considerations
- Public Internet: If deploying on the public internet, ensure that the node is reachable from all parts of the internet. This might involve coordinating with internet service providers and ensuring there are no filters blocking the traffic.
- Internet Exchange Points (IXPs): For nodes deployed at IXPs, it’s essential to ensure that the node can handle the traffic volume typical at such locations. Also, coordination with the IXP operator is crucial.
- Private Networks: If the node is intended for a private network, ensure that it only serves that specific network and doesn’t announce its presence to the broader internet.
Anycast Considerations
Anycast is a method where the same IP address is used by multiple nodes in different locations. This helps in distributing the load and ensuring faster response times.
If using anycast, ensure that all the nodes using the same IP address have consistent configurations and data. This ensures that users get the same response regardless of which node they connect to.
Operational Monitoring
Regularly monitor the node’s operation to ensure its functioning correctly. This includes checking for software updates, monitoring traffic levels, and ensuring that the node is responding to queries as expected.
Coordination
It’s beneficial to coordinate with other AS112 operators, especially when making significant changes or updates. This helps in sharing best practices and ensuring consistent operation across all nodes.
These are the high-level deployment recommendations for AS112 based on the RFC. They provide guidelines to ensure that the node operates efficiently and serves its intended purpose in the broader internet ecosystem.
Security Considerations for AS112
Hosts should ideally never send queries to AS112 servers. Queries related to private-use addresses should be answered locally within a site. If hosts send queries to AS112 servers, they might inadvertently leak information about private infrastructure to the public network. This could pose a security risk.
Logging by AS112 Operators
AS112 operators might log the information they receive. This logged data could be subject to various security and privacy risks. However, these risks exist regardless of whether authoritative servers for these zones are present in the public DNS infrastructure.
Unexpected Traffic
Queries answered by AS112 servers are typically unintentional, meaning the responses from AS112 servers are usually unexpected. Such unexpected inbound traffic might trigger intrusion detection systems or firewalls. AS112 server operators should be prepared for inquiries from remote infrastructure operators who might mistakenly believe their security has been compromised.
Potential Misunderstanding
Operators of AS112 servers might be contacted by individuals who mistakenly believe that responses from AS112 nodes are an attack on their infrastructure. Guidance for those who hold this misconception can be found in [RFC6305].
Loose Coordination
The deployment of AS112 nodes is not as tightly coordinated as other services distributed using anycast. This makes it challenging to detect malicious compromises of an AS112 node or subversion of the data served by the node due to the lack of centralized management.
Potential Attack Vector
Changing the responses to queries received by AS112 nodes might influence the behavior of the hosts sending the queries. Such a compromise might be used as an attack vector against private infrastructure.
Protection Measures
AS112 operators should ensure that AS112 nodes are protected from compromise. Measures similar to those used for production nameservers or network infrastructure should be employed. The guidance provided for root nameservers in [RFC2870] might be helpful.
DNSSEC Considerations
The zones hosted by AS112 servers are not signed with DNSSEC. Given the distributed and loosely coordinated structure of the AS112 service, signing the zones would require the private key material to be effectively public, which would negate any security benefits from using those keys.
In essence, while AS112 provides a valuable service in handling DNS queries for non-routable IP addresses, there are several security considerations that operators and users should be aware of. Proper measures and awareness can help mitigate potential risks.
EdgeUno’s AS112 Implementation
EdgeUno, a leading provider of internet infrastructure in Latin America, has proactively embraced the AS112 project to enhance the efficiency and reliability of its expansive network. Recognizing the importance of handling DNS queries for non-globally unique IP addresses, EdgeUno has implemented AS112 nodes in a strategic manner:
Geographical Spread: EdgeUno’s AS112 nodes are strategically deployed across eight key locations in Latin America. These locations include:
-Colombia
-Mexico, with specific nodes in MEX1, GLD1, and QRO1
-Chile
-Miami (serving as a vital connection point for Latin America)
-Brazil
-Argentina
This widespread deployment ensures that DNS queries originating from various parts of the region are efficiently handled, reducing unnecessary traffic and enhancing user experience.
Technical Specifications
-Operating System: EdgeUno’s AS112 nodes run on servers powered by Linux Debian, a robust and reliable operating system known for its stability and security.
-Routing Daemon: The choice of the BIRD routing daemon ensures efficient and dynamic routing capabilities, allowing the AS112 nodes to effectively manage DNS traffic and respond to queries.
-IPv4 / IPv6 Capable
-Monitoring and Analytics
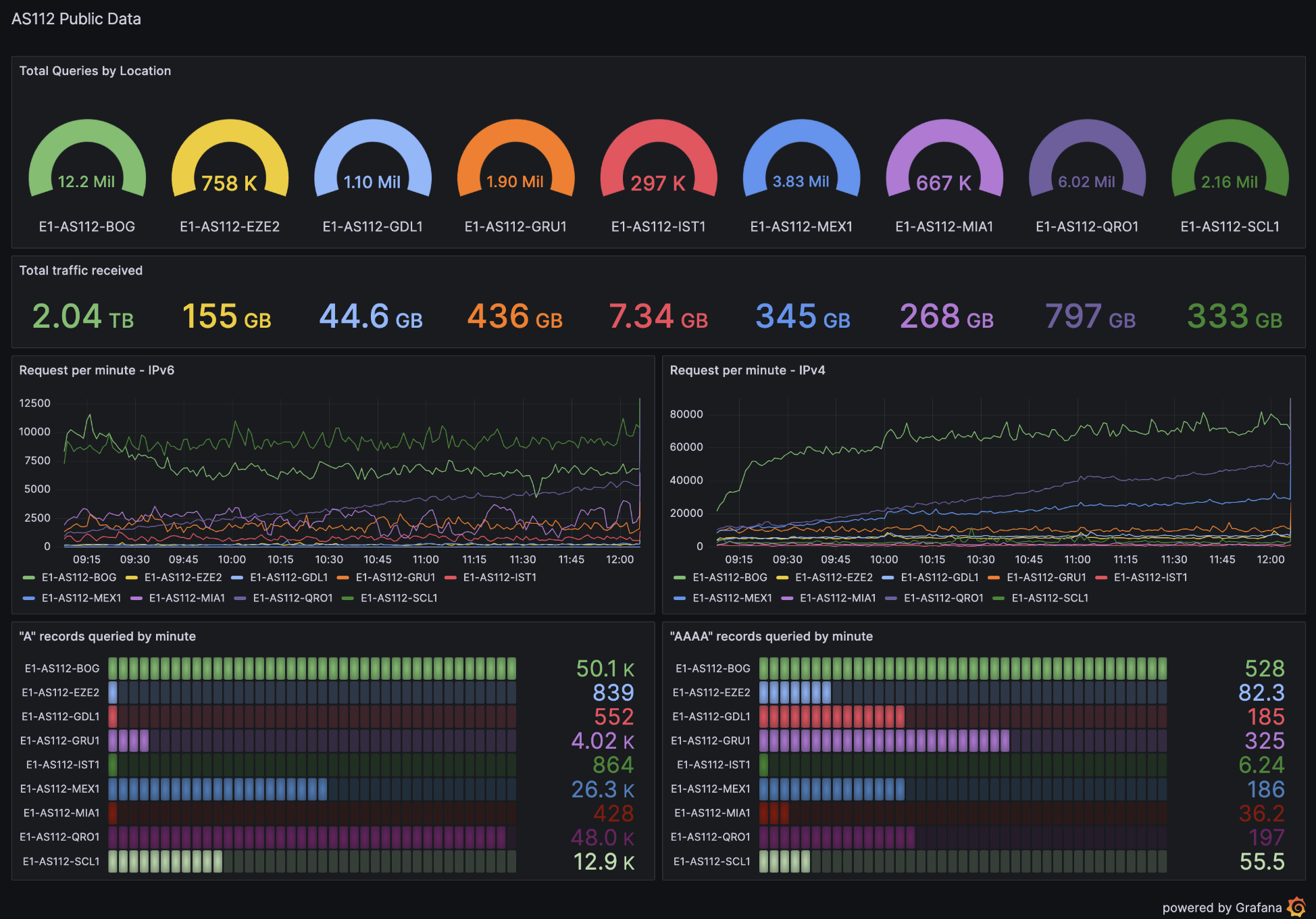
EdgeUno employs a combination of Grafana and InfluxDB for monitoring its AS112 nodes. This setup provides:
Real-time visualization of node performance and traffic through Grafana’s interactive dashboards.
Efficient data storage and retrieval with InfluxDB, ensuring that any anomalies or issues can be quickly identified and addressed.
Call for Action
We invite other networks to consider implementing AS112 nodes within their infrastructure to achieve the following benefits:
- Improve the overall health and stability of the global Internet ecosystem by reducing the load on root DNS servers.
- Enhance local DNS performance and contribute to better network performance for customers.
- Demonstrate commitment to the Internet community by taking a proactive role in maintaining its infrastructure.
- Foster collaboration among network operators and stakeholders to address common challenges and promote responsible Internet practices.
Conclusion
Deploying AS112 nodes is an important and responsible step for organizations managing large networks. By adopting this technical solution, network operators can contribute to a more resilient and efficient Internet, benefiting their customers and the broader online community. Therefore, we encourage other networks to explore the implementation of AS112 nodes and join the collective effort to maintain and enhance the global Internet infrastructure.
References
- RFC 7534 – AS112 Nameserver Operations
- EdgeUno Official Website https://edgeuno.com/
- RFC 1918 – Address Allocation for Private Internets
- RFC 6598 – IANA-Reserved IPv4 Prefix for Shared Address Space